In our previous article we covered all major points related to IPMI protocol risks, and viable solutions to combat these threats, including the configuration of intermediary IPMI proxy servers. Today we intend to push the subject of data security a bit further, and provide you with a detailed preview of yet another backbone feature of the latest EasyDCIM v1.5.2 – ACL (Access Control List).
No matter if working in a production environment or a web app – each user assigned to a specific task must be able to engage with the necessary tools to carry out their job in an optimal way. Does it mean it would be best if everyone had unlimited access to absolutely all resources as well as network and system functions? Of course not. It is not hard to imagine that doing so could seriously endanger the security of the entire company and compromise its stability. What needs to be done instead when using advanced web applications, is developing a proper mechanism for permissions management.
Need for optimization
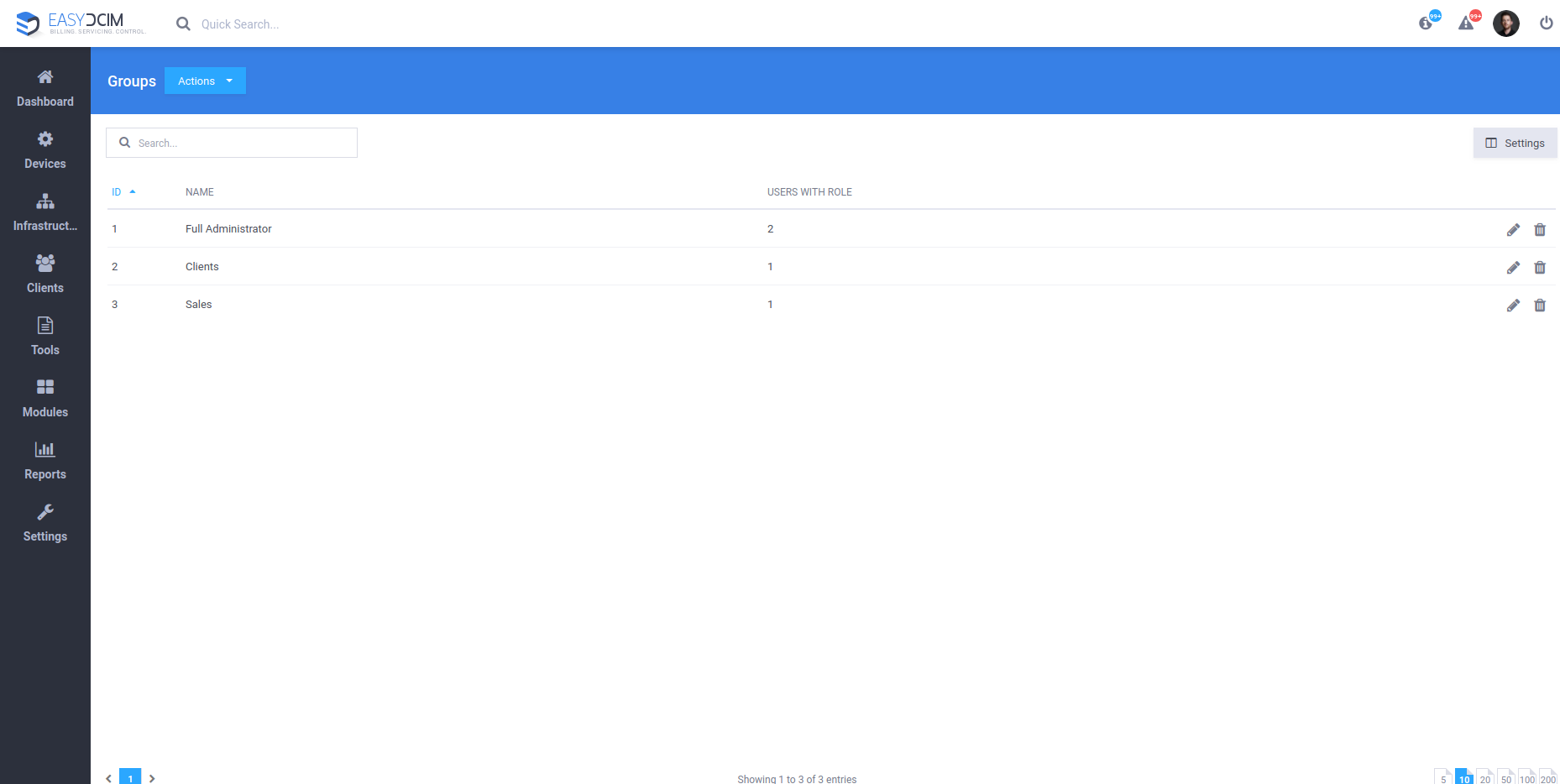
Generally speaking, each user is being assigned to a specific role which defines the set of their available permissions. For example, users belonging to the “Full Administrator” group will have access to every part of the system while the “Sales” group will be permitted to access the pages regarding the management of company orders only. When using ACLs, you may also configure the so-called resources, that is individual rights set per a specific user group. These permissions will define the type of access to selected sections of the system or its functions. What needs to be stressed at this point is that those permissions may be assigned not only to single users, but the whole user groups. Wondering why? Just imagine a situation when you have to give access to the “Orders” section to, let’s say 50 employees. Of course you could click through every single person, changing their permissions. But why would you if you can do this so much faster by creating a new group called “Orders Access” for instance, quickly adding those 50 users and then granting access to the whole group?
Principle of operation
As was already mentioned before, the ACL model is based on distributing permissions to individual user groups. To access the section with group management, navigate to “Settings” → ” Groups”.
By clicking on the desired group and opening the edition window, you can assign to this group appropriate permissions to specific sections of the application. Please note that by default none of the user groups has access to the application’s back-end section. All available permissions are presented in the format of a drop-down tree and are divided into several main sections such as:
1. API Access – defines access to API for a given user through their API key
2. Backend Application Management – specifies if the user should be allowed to log in to the Backend section that covers:
- Clients Management
- Devices Management
- Infrastructure Management
- Modules Management
- Reports Management
- Settings
- Tools Management (system addons)
After the user has correctly logged in to the application, a sidebar menu is being automatically generated, depending on the permissions admitted earlier on to the user group they belong to.
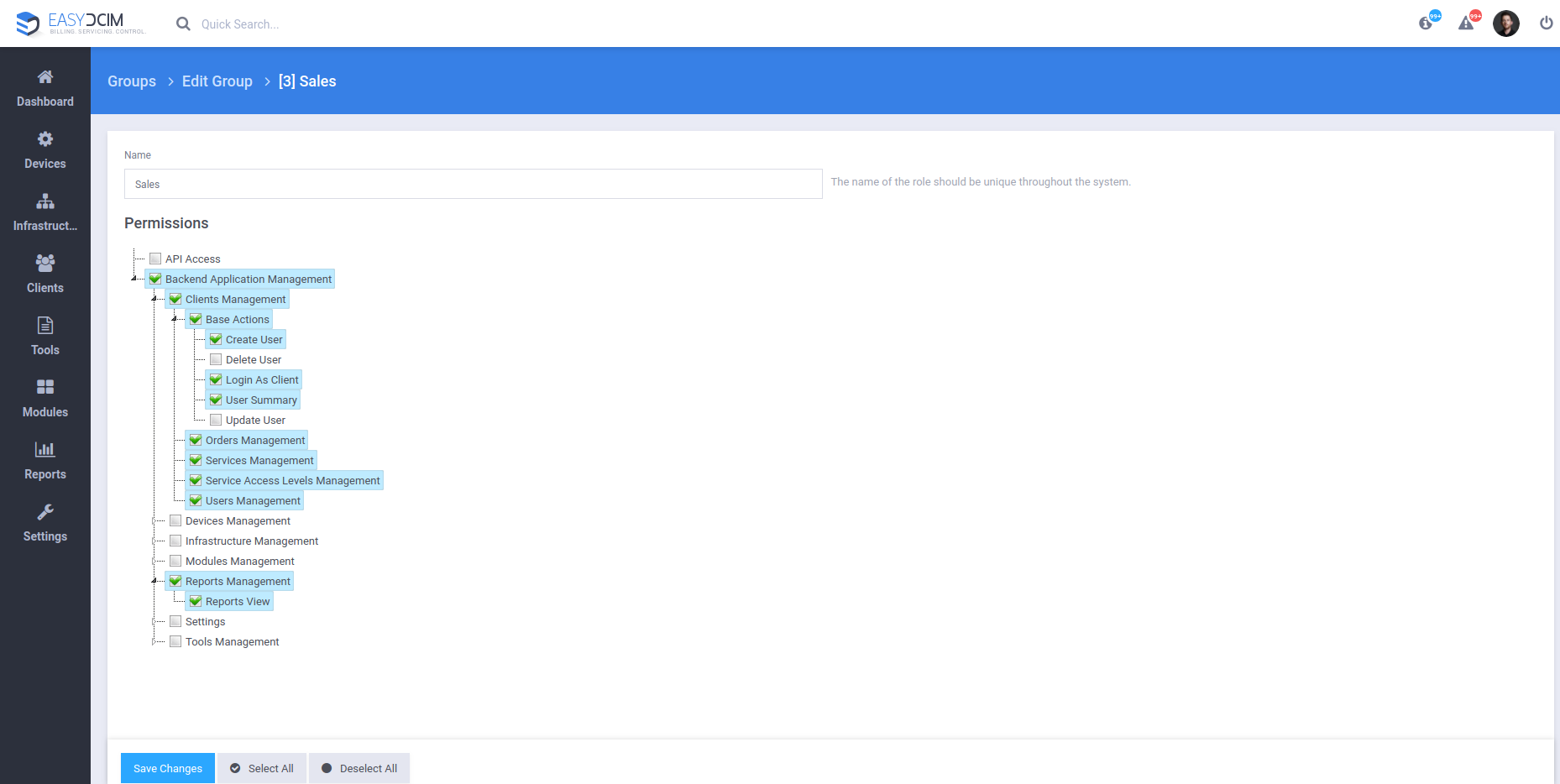
Here, in our example, the user is assigned to the “Sales” group, which has the rights to:
- Log in to the Backend section
- Manage users, orders, and services
- Manage reports
ACL benefits
The first and most obvious advantage derived from the ACL model was already touched upon earlier and revolves around the convenience with which users can be divided into groups and assigned permissions. But another profit that may be even more valuable since it is closely related to privacy, is that the implementation of the ACL model makes the application considerably more safe and less susceptible to attacks. When securing any type of program, it is always the most optimal solution to give users access only to the sections they need. For example, a person who will just manage orders in the company will never need full root privileges, and certainly should not be allowed that much administrative freedom.
The ACL security model allows you to do exactly that – authorize specific groups of users to navigate freely through only those sections that are really required for their tasks, without the worry that they might even inadvertently cause some major complications.
And after all, is there anything more important than making sure your clients’ confidential information is perfectly safe and sound with you, at all times?
Be sure to skim our latest post on IPMI proxy integration, and notes on the EasyDCIM 1.5.2 release as well!